Introduction
One good piece of open source software deserves another right? It is time for a match made in heaven: pfSense and ELSA. pfSense is my favorite open source firewall. I run it in multiple places and it has always been rock solid. If you have read my blog at all you know my appreciation of ELSA. Therefore, I thought it would be a good post to combine the two.
Prepping pfSense
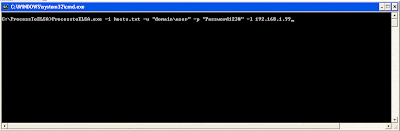
Before you start firing off syslogs to your ELSA server you will need to fix a small issue with pfSense. Apparently, pfSense logs to a binary data file which is then sent to tcpdump to parse. Something in the parsing causes issues with newlines. Single log entries will be sent as two syslogs making parsing them in ELSA (or any other parser) extremely difficult. Fortunately, this site has a simple script and fix for the issue. A PHP script is used to modify the filter file in pfSense. It uses SED in a clever way to weed out all the newlines in the log entries giving you one syslog per entry. You can check out the link above for more information but, I have included the script for convenience. Before you run the script you will probably have to remount the file system as read/write. If you haven't already done so enable SSH on you pfSense firewall to perform these actions.
Mount the file system as read/write
# /etc/rc.conf_mount_rw
$filter=file_get_contents ('/etc/inc/filter.inc');
$filternew =
str_replace(
"-ttt -i pflog0 | logger -t pf -p local0.info",
"-ttt -i pflog0 | /usr/bin/sed -e 'N;s/\\\\n //;P;D;' | logger -t pf -p local0.info",$filter);
if (strcmp($filter, $filternew) !=0) {
file_put_contents('filter.inc.new',$filternew);
file_put_contents('filter.inc.org',$filter);
}
# chmod +x chgfilter.php
# php chgfilter.php
# mv filter.inc.new /etc/inc/filter.inc
Now your pfSense firewall should be syslogging correctly. Just point it at your ELSA server and you should be done configuring it.
Creating the patterndb XML file
First kudos to InfoSec matters blog on configuring Vyatta for ELSA. It made my work a lot easier here. Essentially I used two preexisting ELSA classes, FIREWALL_ACCESS_DENY and FIREWALL_CONNECTION_END, for parsing the pfSense firewall logs. The FIREWALL_CONNECTION_END log is for pass traffic and the FIREWALL_ACCESS_DENY log is for blocked traffic. You might have to turn on logging in pfSense for whatever rules you want to send to syslog. Below is the XML you can add to the patterndb.xml file.
After you have added that code simply restart syslog-ng and all your pfSense firewall logs should be parsing correctly in ELSA.
# service syslog-ng restart
I would like to get some dashboards up soon. The code for the above examples is also on Github. Hopefully, that will be another blog post in the near future. As always, I welcome your comments and feedback.